Introduction
Thank you for reading this post, don’t forget to subscribe!
In the ever-expanding digital universe, the security of an organization’s network is paramount. A critical component of this security infrastructure is the firewall. Originally conceptualized as a barrier to prevent unwanted network traffic, the firewall has evolved into a sophisticated tool that does much more than just guard the gate. In this blog, we will explore what a firewall is, its types, and why it is an indispensable asset for any organization.
What is a Firewall?
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. Its primary objective is to establish a barrier between your internal network and incoming traffic from external sources (such as the internet) to block malicious traffic like viruses and hackers.
Types of Firewalls
-
Packet-Filtering Firewalls
The most basic type of firewalls, they inspect packets (small chunks of data) against a set of filters. Packets that make it through the filters are sent to the requesting system and all others are discarded.
-
Stateful Inspection Firewalls
These firewalls keep track of the state of active connections and make decisions based on the context of the traffic, rather than just individual packets.
-
Proxy Firewalls (Application-Level Gateways)
These firewalls act as an intermediary between two end systems. The firewall receives and scrutinizes incoming data packets, then sends them to the receiving system, blocking harmful content.
-
Next-Generation Firewalls (NGFW)
These combine the capabilities of the traditional firewall with additional functionalities like encrypted traffic inspection, intrusion prevention systems, and more, for more comprehensive protection.
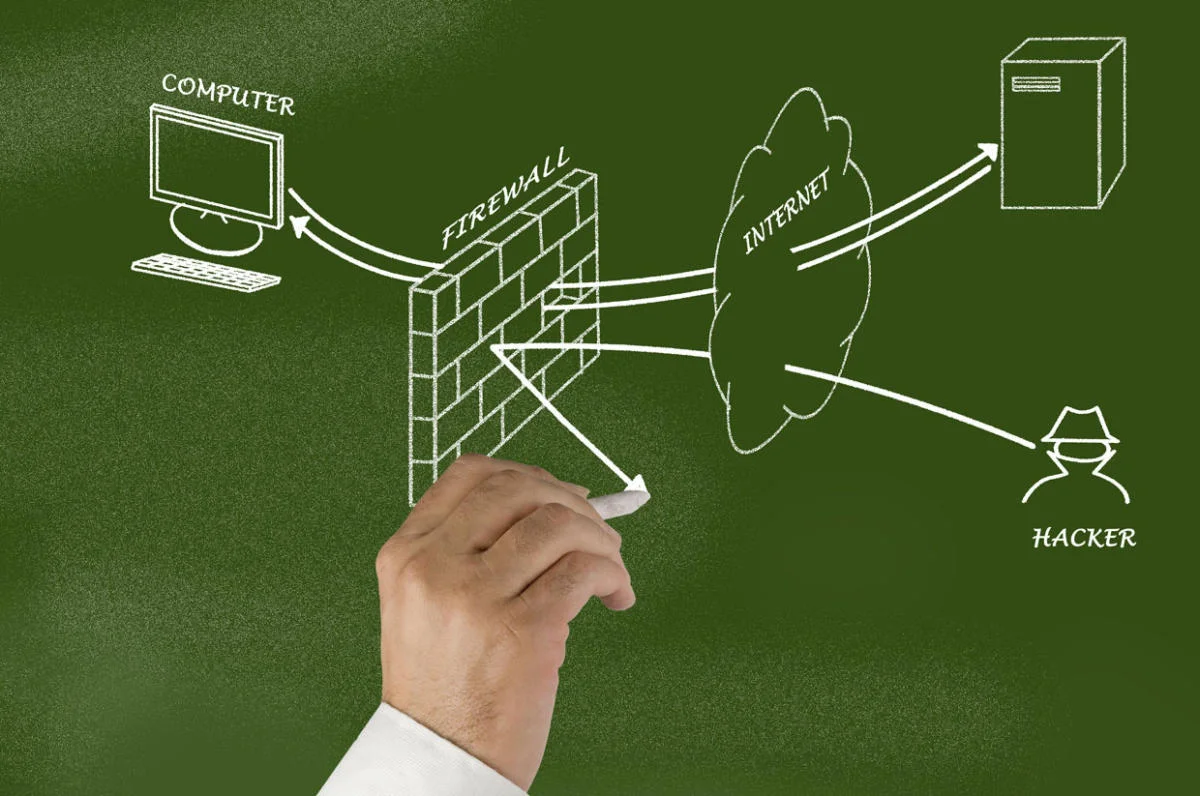
Why are Firewalls Essential for Organizations?
-
Protecting Sensitive Data
One of the primary reasons organizations use firewalls is to protect sensitive data. By controlling incoming and outgoing traffic, firewalls help prevent data breaches and unauthorized access to sensitive information.
-
Blocking Malicious Traffic
Firewalls are crucial in detecting and blocking malicious traffic like malware and cyber-attacks. By setting specific security rules, firewalls can help keep out potential threats.
-
Regulatory Compliance
Many industries have regulations that require data protection and network security. Firewalls help organizations comply with these regulations, avoiding legal issues and fines.
-
Preventing Unauthorized Remote Access
A firewall can prevent unauthorized remote access by limiting network access to authenticated and authorized users only.
-
Segmenting the Network
Firewalls can be used to segment networks, creating ‘zones’ with different security levels. This is especially important for large organizations with diversified departments and functionalities.
Best Practices for Firewall Management
– Regular Updates and Maintenance: Keep the firewall’s firmware and software updated to protect against the latest threats.
– Strong Configuration: Ensure that the firewall is configured properly to protect the network without hindering legitimate traffic.
– Regular Monitoring: Continuously monitor firewall logs to detect and respond to suspicious activities quickly.
– Integration with Other Security Tools: Use firewalls in conjunction with other security tools like antivirus software and intrusion detection systems for layered security.
Conclusion
A firewall is much more than just a part of your IT infrastructure; it is a vital component of your organization’s cybersecurity strategy. It not only protects your network from external threats but also helps in managing and monitoring network traffic. In today’s world, where cyber threats are constantly evolving, a robust firewall is not just a recommendation, it is a necessity. As technology continues to advance, the role of the firewall will only grow in importance, making it an indispensable tool in the arsenal against cyber threats.








